The purpose of this document is to provide configuration of the AD FS service to authenticate vCloud Director users on the Organization level.
I would like to thank to Johan Bogema for his input in this procedure. Further information on SAML authentication with vCloud Director can be found on his blog.
http://www.bogema.eu/saml-authentication-failed-organization/
Requirements:
– Windows Server 2008/2012
– Active Directory service installed
– Active Directory Federation Service Installed
– IIS installed
– VMware vCloud Director 5.1/5.5/5.6
AD FS installation
1. Open Server manager to add AD FS role on Windows Server.
2. Click next.
3. Choose Role-based or feature-based installation
4. Select the server that you wish to use of AD FS role.
 5. Choose Active Directory Federation Services from the list
5. Choose Active Directory Federation Services from the list
6. Accept additional roles that are required for AD FS.
7. Leave defaults and click Next
8. Accept defaults.
9. Click install to add AD FS role.
Generating IIS certificate
Before configuring AD FS, the self-signed or signed certificate has to be generated for IIS server.
1. Open Internet Information Services (IIS) Manger
2. Click on the server in the left pane and choose Server Certificates
3. Create Self-Signed or Signed certificate. (Self-Signed certificate will be used for this procedure)
AD FS configuration
1. Run AD FS Management tool.
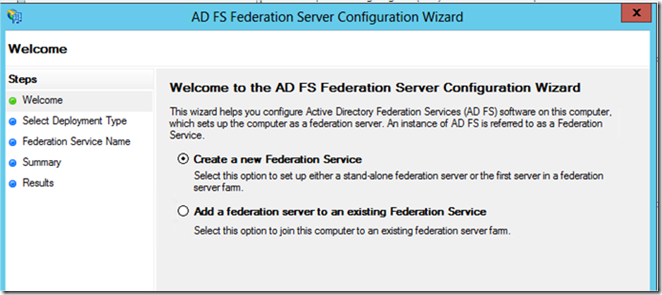
2. Run AD FS Federation Server Configuration Wizard
3. Choose Create a new Federation Service
4. Next choose Stand-Alone federation server.
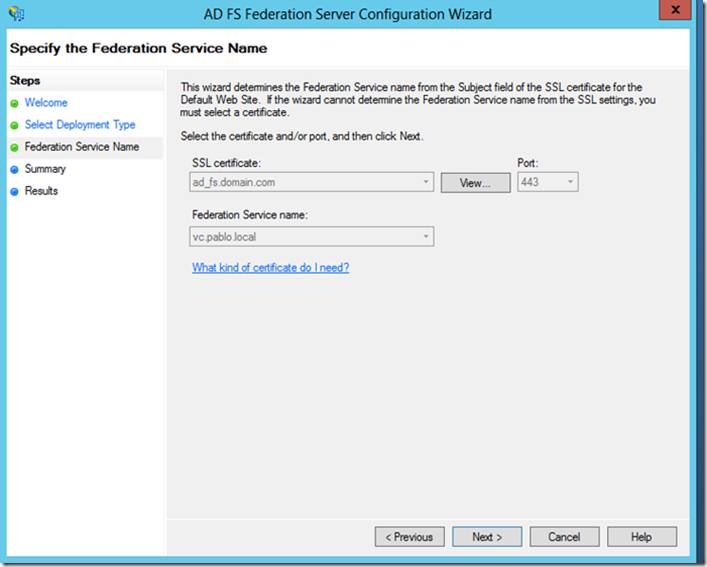
5. Choose SSL certificate and click next to complete the configuration.
vCloud Director configuration
1. Verify that vCloud Director and AD FS server have exactly the same time. Even the small difference will fail the login process.
2. Download SAML metadata XML file from AD FS server by following the link below.
https://<ADFS Server URL>/FederationMetadata/2007-06/FederationMetadata.xml
3. Go to vCloud Director Web UI and open the target Organization. Choose Administration and next Federation.
4. Click on Use SAML Identity Provider and next on Browse to add xml file downloaded from AD FS server.
5. Verify if the certificate is not expired. If it is click on Regenerate to issue the new one.
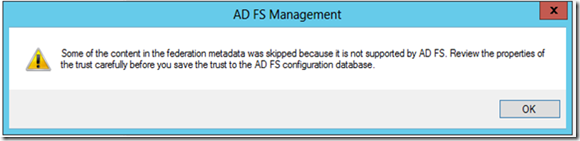
6. The final Federation setup window should look like the following example. Apply the changes.
Creating Relying Party Trusts in AD FS service.
1. If the vCloud Director has self-signed certificate, download the certificate and install in the AD FS keystore as Trusted Root CA and Third Party Trusted Root CA.
2. Run AD FS Management tool.
3. Choose Relying Party Trusts in the left pane.
4. Choose Add Relying Party Trust… in the right pane.
5. Choose first option and enter the following template link.
https://<vcloud.domain.com>/cloud/org/<organizationname>/saml/metadata/alias/vcd
6. Accept the warning.
7. Give the display name that will identify the target organization.
8. Choose Permit all users to access this relying party
9. Click Next to complete the configuration.
10. Finish the wizard, and then go ahead to edit the properties of the Relying Party Trust you just created. In the Advanced tab, you have to change the Secure hash algorithm to SHA-1.
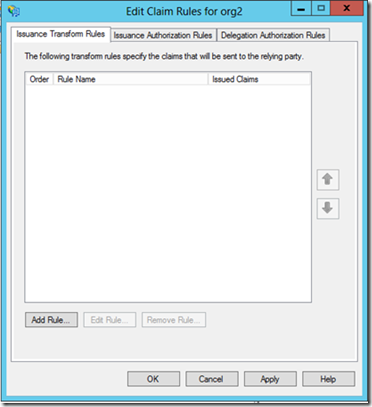
11. Click on the configured Relying Party Trust and choose Edit Claim Rules… in the right pane.
12. Click on Add Rule… in Issuance Transform Rules tab.
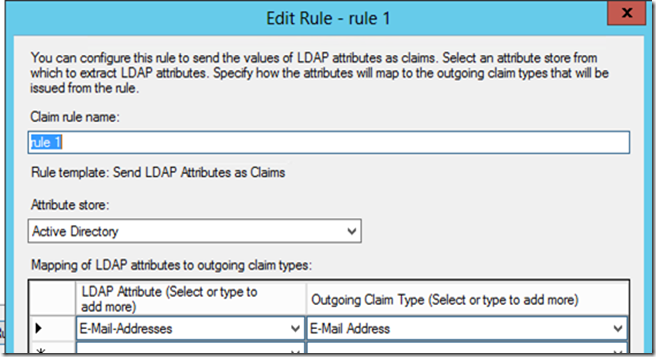
13. Select Send LDAP Attributes as Claims and click Next.
14. Name the rule. Choose Active Directory in Attribute store field. Set the mapping as per following screenshot. Click Finish.
15. Add another rule and choose Transform an Incoming Claim as Claim rule template. Fill in as follows and click Finish once completed.
Bits and pieces.
1. Import SAML users to Organization and test login process.
2. ADFS authentication process will use “username@domain.com” login format. It will compare email address that is in properties of the AD account and SAML user name from vCloud Director. If AD account will be missing the email address value the authentication will fail on the vCD side.
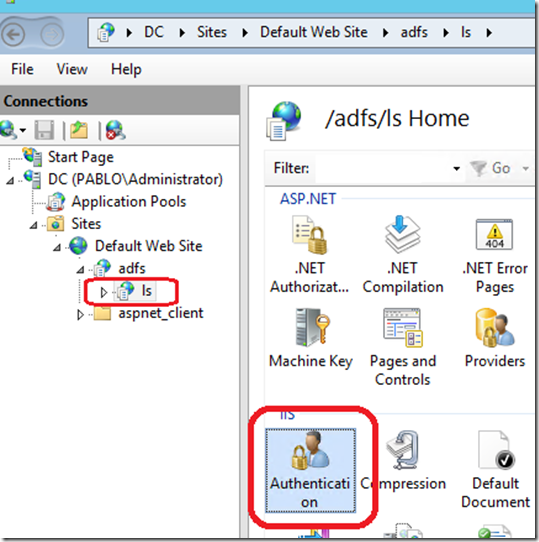
3. The AD FS default login window will be Windows like form. This can be changed to Web Form view by:
a. editing C:\inetpub\adfs\ls\web.xml file and changing following items.
– <authentication mode=”Forms” />
– <localAuthenticationTypes>
<add name=”Forms” page=”FormsSignIn.aspx” />
<add name=”TlsClient” page=”auth/sslclient/” />
<add name=”Basic” page=”auth/basic/” />
</localAuthenticationTypes>
b. enabling Form Authentication and disabling Windows Authentication on ls website as per following screenshots.
4. If the Federation Certificate in Organization will be regenerated the change has to be applied to the corresponding Relying Party Trust by choosing Update from Federation Metadata… in AD FS Manager tool.























Hi, im encountering issues related to SAML authentication. What Windows version are you using Windows 2012 or Windows 2012 R2? What vCloud Director version also? Appliance or the Bin installation. Thanks.
LikeLike
Hi Billy,
This was tested on Windows Server 2008 R2, 2012 and 2012 R2 with self signed certificates on ADFS and vCloud Director side.
vCloud Director versions were 5.5.2 and 5.6.3. Both were Bin as Appliance should be used only of proof of concept.
What errors do you see in the ADFS server and vCloud Director debug logs?
Regards
Pawel
LikeLike
Here’s the error screenshots that im getting: 1. http://picpaste.com/SAML-ERR1-LRex6qbV.JPG ; 2. http://picpaste.com/SAML-ERR2-KlGLq3k4.JPG ; 3. http://picpaste.com/SAML-ERR3-YHPcNjbJ.JPG / I’ve also check the time for the VMs (AD, ADFS, VC, VCD) everything are in sync. I’ll post the error that im getting here. Initially im using the VCD appliance, 5.6.3 and Windows 2012 R2. I’ll try to use the Full Bin installation, maybe that would make a difference.
LikeLike
Billy,
According to the screenshots it looks like the issue is in vCloud Director as ADFS passes the authentication.
Please connect to vCloud Director command line and look for errors in vcloud-container-debug.log file that is located in /opt/vmware/vcloud-director/logs/.
Is vCloud Director uses external NTP server or local? Is it the same as ADFS server?
Regards
Pawel
LikeLike
Im configuring the ADFS now using your steps and integrate it with VCD for the SAML part. I’ll configure VCD to use an external NTP, same with VC and AD to make sure no issues with time. I’ll post the errors here in the log file if i get the same. Im using Windows 2012 Standard Edition for AD & ADFS + vmware-vcloud-director-5.5.2-2233543 with vCenter 5.5.20400 appliance . Crossing my fingers!
LikeLike
Billy,
I’ve found that procedure is missing one step.
The user account that is used for SAML authentication has to have an email address in the email filed of the AD user properties.
The Claim Rules that are configured in Relaying Party Trust are matching email address of the AD account through LDAP queries and Organization Administrator that was added as SAML user.
The format on both sides has to be “username@domain.local”.
Regards
Pawel
LikeLike
Got it. Will make sure to configure the email address field of the AD user property. Im still doing the integration of ADFS & VCD. Will post immediately any issues that im encountering. I’ve make sure VMware Tools are all installed in the VMs (AD, ADFS & VCD). Same thing also in configuring external NTP for AD, VC & VCD.
LikeLike
Billy,
The best would be to have all VMware products pointed to the same nearest internal NTP server and then configure that internal NTP server to source time information from the external one. With this scenario any external network outages won’t affect time sync internally.
Regards
Pawel
LikeLike
Got it. For the logs any idea, where can i upload it for analysis? It might be too big for me to post everything here. I’ll upload again the error screenshot once i get it.
LikeLike
My First Error, opening the ADFS page: http://picpaste.com/SAML-Error1-ElhxJl5m.JPG
LikeLike
2nd Error: http://picpaste.com/SAML-Error2-dj1jjsal.JPG
LikeLike
Will try to install ADFS, i think this error is related to it, not completing the installation properly. Though it seems OK, server manager hang on the last minute of the installation and i forcibly close it, maybe it wasnt able to install all the needed files.
LikeLike
Login is OK -> http://picpaste.com/SAML-Logon-HHyqAjoU.JPG / Got this Error after selecting VSS OrgVDC Portal -> http://picpaste.com/SAML-Error3-M47OS6JY.JPG / I’ll check the logs.
LikeLike
Here’s the VCD logs that i have -> http://wikisend.com/download/841514/VCD-logs.zip
LikeLiked by 1 person
Billy,
I’ve checked the logs and I’ve found the following errors in vcloud-container-debug.log.
2015-03-11 02:48:33,928 | ERROR | pool-jetty-85 | CertPathPKIXTrustEvaluator | PKIX path construction failed for untrusted credential: [subjectName=’CN=ADFS Signing – SSO.adfs.lab’]: unable to find valid certification path to requested target |
2015-03-11 02:48:33,929 | ERROR | pool-jetty-85 | SignatureValidationFilter | Signature trust establishment failed for metadata entry http://SSO.adfs.lab/adfs/services/trust |
2015-03-11 02:48:33,930 | ERROR | pool-jetty-85 | AbstractReloadingMetadataProvider | Error filtering metadata from vss |
org.opensaml.saml2.metadata.provider.FilterException: Signature trust establishment failed for metadata entry
According to that your SSL certificate of SSO server has incorrect CN entry. The vCD is looking for “CN=ADFS Signing – SSO.adfs.lab” instead of “CN=SSO.adfs.lab”. You should re-generate the SSL certificate with the correct CN value. Be aware that CN has to always match FQDN or IP address of the server.
Once you fix the SSL cert, you will have to present it to ADFS again.
Regards
Pawel
LikeLike
Thanks alot. You’ve been very helpful. I appreciate it very much!
LikeLike
You’re welcome. Happy to help.
LikeLike
Hello,
I am using vCloud SAML now in our organization. I configured it by sending the Group-membership as a claim type. Users are now automatically added if they are member of one of the 3 service level groups i configure in vCloud. This all works perfect thanks to your article!
Although i have one problem which i cant seem to fix. A user is automatically added but the contact info like Full Name, Mobile Phone are not filled in. How can i configure ADFS to send the claim types like Display-Name so vCloud fills this in the contact info? I already tried custom claim rules like:
=> issue(Type = “FullName”, Value = “Max”);
It seems the only claim that is working and added to the user details is Name ID. This is being used as e-mail address and username.
Hope you can help me!
Max
LikeLiked by 1 person
Just to let everyone know, this issue has been resolved in vCloud Director 5.6.5 and 8.0. There is no information about the next version of vCD 5.5 so upgrade is the only option for now.
LikeLike
Hey Max, we are trying to do the same you are doing. Can you help us in how you exactly send the Group Membership to the vCloud. Are you setting the SAML User in vCloud to the Role “Defer to identity” and use “Organization Administrator” as a claim or did you import a SAML group like “orgusers” and set a role “Organization Administrator” for this group and send the claim type “orgusers” over?
Thank you for your help
LikeLike
Pingback: vCloud Director and SAML Federation – Funky Cloud Medina
Hi,
We completed the setup with VCD/DUO(with ADFS)–>First auth is AD credentials and second auth will be DUP push(to my mobile).Everything is working fine.After approving the DUO push from my mobile,it is landing to VCD page where we are getting error “SAML authentication failed for this organization”
“Use integrated authentication”.If i use this Integrated auth(VCD local account),everything will work.How to mitigate the SAML auth issue ? Any ideas?
Thanks,
Manivel R
LikeLike
Hi Team,
We are trying to introduce 2factor authentication for our vCloud director(VMware) with the help of DUO security.
Im getting the SAML authentication failed error at the final stage and dont know where i need to check? Could you please advise. Im suspecting something here in ADFS relying party trust.
1) DUO admin console(GOT JSON file from here)
2) DAG(linux machine)—>Active Directory is acting as a authentication source(In DAG URL(at the metadata section),at the bottom,we got the XML file of DAG)
3) vCloud director—-> We got the SAML metadata(i.e VCD XML file).
3) AD server—>In relying party trust(ADFS)
Process
1) DUO JSON file downloaded and then uploaded the JSON file in DAG gateway(Application section)
2) In DAG,we downloaded the XML file in application’s metadata section and uploaded the XML file under Vcloud director Federation “SAML” section.
3) In vCloud director,we downloaded the XML file from SAML field and uploaded the same file in relying party trust(ADFS)i.e AD server.
When i try to login the vCloud director,
1) First authentication is AD credentials—>Its successful
2) Second authentication is DUO push—->Its successful.
3) After landing in to vcloud page,i got an error as https://globalvcd.usinternal.com/cloud/failure.jsp
Error is SAML authentication failed for this organization.
2019-08-21 05:02:17,763 | DEBUG | pool-jetty-70 | CustomWebSSOProfileConsumerImpl | Validation of authentication statement in assertion _4756984f02c6a40c1e64fa24782790752934f60930 was successful | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,763 | DEBUG | pool-jetty-70 | CustomWebSSOProfileConsumerImpl | Including attribute sAMAccountName from assertion _4756984f02c6a40c1e64fa24782790752934f60930 | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,763 | DEBUG | pool-jetty-70 | CustomWebSSOProfileConsumerImpl | Including attribute mail from assertion _4756984f02c6a40c1e64fa24782790752934f60930 | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,763 | DEBUG | pool-jetty-70 | CustomWebSSOProfileConsumerImpl | Including attribute duo_username from assertion _4756984f02c6a40c1e64fa24782790752934f60930 | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,763 | INFO | pool-jetty-70 | SAMLDefaultLogger | AuthNResponse;SUCCESS;10.128.7.39;https://globalvcd.usinternal.com/cloud/saml/metadata/alias/vcd;https://globalduolab.usinternal.com/dag/saml2/idp/metadata.php;rrajarathinam@xxx.com;; | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,764 | DEBUG | pool-jetty-70 | CustomSamlProcessingFilter | Authentication success. Updating SecurityContextHolder to contain: org.springframework.security.providers.ExpiringUsernameAuthenticationToken@b277c90f: Principal: rrajarathinam@xxx.com; Credentials: [PROTECTED]; Authenticated: true; Details: null; Not granted any authorities | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,771 | ERROR | pool-jetty-70 | JDBCExceptionReporter | ERROR: syntax error at or near “)”
Position: 136 | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,777 | WARN | pool-jetty-70 | SamlAuthenticationSuccessHandler | Error logging in user name=rrajarathinam@xxx.com, email=rrajarathinam@xxx.com, groups= | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
2019-08-21 05:02:17,777 | DEBUG | pool-jetty-70 | SamlAuthenticationSuccessHandler | Login failure details for user name=rrajarathinam@xxx.com | requestId=26f60f01-5ff1-4d08-b678-86209157fafe,request=POST https://globalvcd.usinternal.com/cloud/saml/SSO/alias/vcd,requestTime=1566378137528,remoteAddress=10.128.7.39:57755,userAgent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 …,accept=text/html application/xhtml+xml application/xml;q 0.9 image/webp image/apng */*;q 0.8 application/signed-exchange;v b3
org.hibernate.exception.SQLGrammarException: could not execute query
at org.hibernate.exception.SQLStateConverter.convert(SQLStateConverter.java:90)
at org.hibernate.exception.JDBCExceptionHelper.convert(JDBCExceptionHelper.java:66)
at org.hibernate.loader.Loader.doList(Loader.java:2231)
at org.hibernate.loader.Loader.listIgnoreQueryCache(Loader.java:2125)
at org.hibernate.loader.Loader.list(Loader.java:2120)
at org.hibernate.loader.criteria.CriteriaLoader.list(CriteriaLoader.java:118)
at org.hibernate.impl.SessionImpl.list(SessionImpl.java:1596)
at org.hibernate.impl.CriteriaImpl.list(CriteriaImpl.java:306)
at org.hibernate.impl.CriteriaImpl.uniqueResult(CriteriaImpl.java:328)
at sun.reflect.GeneratedMethodAccessor175.invoke(Unknown Source)
at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43)
LikeLike